Written by Craig Atkins, Managing Director, 1-Fix Limited
It is estimated that the healthcare cybersecurity market will be worth $26.1 billion by 2027, according to recent market research by Meticulous Research®. The demand for advanced cybersecurity is mainly driven by large-scale cloud adoption paired with the emergence of increasingly complex cyber threats.
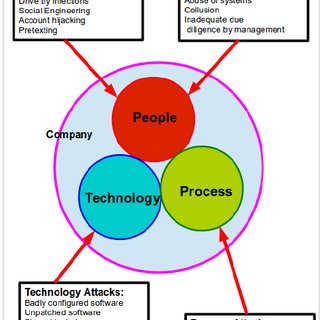
Healthcare organisations must balance the business benefits of embracing cloud adoption which transforms the delivery and accessibility of healthcare services against the legal and reputational backlash or a hack or data leak of sensitive patient data.
A prolific example was the WannaCry ransomware outbreak in 2017. While not specifically targeted against the NHS, WannaCry exposed the lack of investment of many NHS trusts in their IT infrastructure. After a breach, the key is understanding what went wrong and why so the appropriate improvements to minimise future similar risks can be made.
Patching
The leading cause of worm-like cyber threats spreading around all IT systems is due to them exploiting a vulnerability in the operating system or third-party software that has been installed on the network.
If you outsource the management of patching to an external Managed Service Provider (MSP) then ensure your IT Director, CISO or similar responsible person understands how these patches are applied, what is being patched and at what frequency.
Utilise a third party to test for patch compliance. If you outsource to an MSP then use your internal team or an external IT security consultancy to run a vulnerability scan to ensure you do not fall victim to a team that claims to be patching, but is not delivering.
You can utilise a number of software/SaaS tools to automate the vulnerability scanning – such as Nessus (https://www.tenable.com/products/nessus) or OpenVAS (https://www.openvas.org/). While it is advisable to work with security experts to interpret and close discovered issues, the tools above will highlight patch issues and scan using known common vulnerabilities.
Ensure your patching and management extends to all areas of the network and cloud services. Do not forget Azure/AWS or similar platforms that you are expected to secure.
Patching and closing security vulnerabilities is harder with full SaaS offerings, as you do not typically have any access or control of the software or underlying infrastructure. However, you can still check for vulnerabilities or run scheduled penetration testing on these services but ensure you use your own security consultants to run the penetration testing. Do not let the vendors “mark their own homework”.
Leaks
Over the past decade huge amounts of personal data have been leaked to the internet via misconfigured data stores – known as buckets in the Amazon Web Services’ (AWS) world.
Security mistakes have allowed hackers to stumble across databases of private data which should not be accessible to anyone outside the organisation.
If your IT team are working with AWS, Microsoft Azure, Google Cloud or other public cloud providers then ensure that you have the skills in-house to secure and test the security of these cloud instances. If you do not, then outsource a security audit to a professional security firm who specialise in the cloud platform you use.
Cloud restrictions
While cloud-based systems can be accessed anywhere, that does not mean they should be, especially in healthcare. Data access requirements and controls within healthcare should be replicated in cloud systems. This should filter down to physical access to the systems, as well as to individual patient records.
For example, access to write medical imaging data into a PACS (Picture archiving and communication system) should be locked to the specific devices and locations that need this functionality, and not left open to the entire network.
Auditing your key systems is a good place to start. Look at what data is stored, how classified it is, who needs access and where from. Then work with your IT team and SaaS vendors to mirror your requirements on the firewalls, access control lists and user permissions. Once the audit is complete ensure you have proper information management controls to handle requests for new users, permission uplifts, changes and alterations, and other odd cases that may require a temporary or permanent change to your permission structure. Schedule a regular audit process to pick up outliers or non-compliant users and the incorrect permissions.
Security tools
SaaS vendors often offer a range of security tools within their products, many of which are not enabled out of the box. You should use features such as multi-factor authentication (MFA or 2FA), password strength requirements, and conditional access based on location or device profiles to provide a solid security baseline.
Data logs
All SaaS applications and physical systems produce logs, and most major SaaS applications allow the exporting of these logs to a security information and event management (SIEM) platform.
Depending on the size of your organisation, you may have a security operations centre (SOC) either in-house or outsourced. If you do, then they will have a SIEM platform they want you to feed into, so ensure you keep them involved and informed of new SaaS systems you are planning to implement. If you do not currently work with an SOC, you should consider doing so. Having security logs in place and not monitoring them means you are always reactive to security threats if you are even aware of them at all.
If your size or budget does not warrant a SOC, then ensure you gather and keep the logs at minimum. This allows you to bring in forensic data breach investigators in the worst-case scenario.
The post Craig Atkins: Cyber security when managing sensitive patient data in healthcare appeared first on .